- About O-ISM3
- O-ISM3 Services
-
Featured Articles
- Ask Smart Questions to Set Security Service Levels
- Ten ways ISMS fail
- Can you pass the O-ISM3 Test?
- Advanced Classification of Information
- What is the Maturity of your ISMS?
- A primer in Metrics driven Process Management
- Risk, Investment and Maturity
- Return On Security Investment
- Process Management with Security Metrics
- Measuring Security
- Compliance vs Continuous Improvement
- How can you Measure how Secret a Secret is?
- Beyond Authentication, Authorization and Accounting
-
by Vicente A. Canal
- Slideshare
- Youtube
- Contact
O-ISM3 Security Body of Knowledge
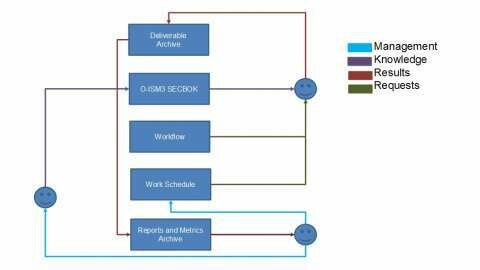
O-ISM3 SECBOK is an Information Security Management System implementation template based on the O-ISM3 standard. It assists the creation of ISMS for organisations of any size, environment, and with any availability of resources Buy now your copy of O-ISM3 SECBOK and take your ISMS to new heights!
To obtain the maximum benefit from O-ISM3 SECBOK, the organisation uses O-ISM3 SECBOK's documents, templates, examples and data schemas to formalize the organisation's day-to-day management system and activity in information security in a model that follows a methodology of continuous improvement. Formalizing the management system and daily activity following the scheme marked by O-ISM3 SECBOK has the following effects on the performance of the organisation:
- When undocumented knowledge decreases, dependence on specific individuals or providers is lower.
- When knowledge is documented, different people or companies can perform activities with an equivalent level of quality. This increases competition and improves the negotiating position of the organisation when contracting services. It is simpler, and therefore increases the flexibility to temporarily replace people for vacations, courses or events, which improves the work environment.
- By documenting knowledge, external audits entail little additional effort for the organisation.
- When a change or improvement is introduced in an activity, this improvement reaches the whole team, even when it is large or distributed in time or space quickly. This facilitates continuous improvement.
- Between 30 and 40 percent of the working time is frequently used in determining what activity to do or how to do it. Documenting knowledge reduces this time in half, releasing time to perform useful activity and therefore improving the performance of work teams.
- The management of tasks by deliverables makes the distribution of responsibilities objective, not subjective, which improves coordination and relationship with the rest of the organisation.
- There is an equivalence between the activity performed and what is reported.
- The managers have all the information necessary to identify if the changes introduced give the expected results and what changes are necessary to improve the achievement of objectives or performance.
Due to the structure of O-ISM3, it has built-in references to standards, and cross-references can be easily incorporated that significantly decrease the effort associated with regulatory compliance. By default, O-ISM3 has references to ISO27001, and the British schemes of Information Governance and Cyber Essentials.
O-ISM3 SECBOK improves the visibility of processes for management, thanks to a direct connection between planning, metrics, reporting, and management or improvement decisions.
Documentation of processes covers What (Description), How (Supporting Documentation), When (Planning), Where (Supporting Documentation), Who (Internal Responsibilities), Why (Benefits), and the Deliverables Repository contains the evidence of the Activity, so that all aspects of an Audit are covered by default.
Who can benefit from O-ISM3 SECBOK?
- Those who are using ISO9001: Build your ISMS using ISO9001 principles and infrastructure you already have and understand;
- For someone who has no IS Management System: Build your ISMS in stages around your Business Goals, not some external or artificial goals;
- For someone who wants to outsource security processes: Find out exactly what to outsource, who to link it to internal processes and how to create SLAs;
- For someone who already has Information Security Targets: Use Security Targets and learn at least if the IS management system is working, or use Metrics and manage your IS management system with or without Auditors;
- For someone who is experiencing pains using other approaches: Suit you processes to your needs in an environment by environment basis. Stop using Production Environment requirement for your Development Environment;
- For a CISO: Get to tell Top Management, Middle Management and Administrators what are their responsibilities on security, in a more specific way than "Security is everyone's responsibility";
- For businesses that are going out to tender for their services;
- For businesses that require a consistent approach by all service providers in a supply chain;
- For service providers to benchmark their IT service management;
- As the basis for an independent assessment;
- For an organisation, which needs to demonstrate the ability to provide services that meet customer requirements;
- For organisations, which aims to improve service through the effective application of processes to monitor and improve service quality.
List of O-ISM3 documents and templates
O-ISM3 SECBOK is an Information Security Management System implementation template distils ten years of experience implementing O-ISM3 and represent a large head start for any consultant or company who implements a highly mature ISMS based on O-ISM3. A partial list of documents, including guidance, forms, policies, templates, sample procedures, sample reports, follows:
Management report template, that includes Compliance, Performance, Governance, Risk and Maturity aspects:
Agreements
- Acceptable Use Agreement
- Non-disclosure Agreeement
Forms and Checklists
- Information Security Awareness Training Completion Form
- Personal Information Sharing Consent Form
- Training Record Form
- User Registration Assessment Form
Lists
- List of Documents and Definitions
- List of Policies
- List of Single Points of Failure
- List of Third Parties Form
Plans
- Business Continuity Incident Meeting Agenda
- Information Security Improvement Plan
Policies
- Asset Disposal Policy
- Bring Your Own Device Policy
- Business Continuity Policy
- Change Management Policy
- Classification of Systems and Information
- Clear Desk and Clear Screen Policy
- Cryptographic Controls Policy
- Data Protection and Confidentiality Policy
- Freedom of Information Act Policy
- Identity Management Policy
- Information Governance Policy
- Information Security Policy
- Mobile Computing and Teleworking Security Policy
- Network Security Policy
- Outsourcing of Information Security Services Policy
- Risk Management Policy
Procedures
- Alerts Monitoring Procedure
- Asset Disposal Procedure
- Business Continuity Incident Procedure
- Using O-ISM3 SECBOK Procedure
- Compliance and Legal Request Procedure
- Confidentiality Audit Procedure
- Data Centre Access Procedure
- Data Centre Monitoring Procedure
- Identification and Assessment of new Processes and Information Assets Procedure
- Individual Business Continuity Procedure
- Inventory Procedure
- Leavers Procedure
- Maturity Assessment Procedure
- Patching Management Procedure
- Penetration Test Remediation Procedure
- Risk Assessment Procedure
- Risk Treatment Procedure
- Secure Transfer and Receipt Personal and Sensitive Information Procedure
- Security Awareness Procedure
- Security Incident Management Procedure
- Starter Procedure
- Workload Schedule and Metrics and Reports Procedure
- Workload Schedule and Metrics Template Procedure
Schedules
- Business Continuity Schedule
- Work Schedule and Metrics O-ISM3.xlsx
Specs
- Alerts Monitoring Process Spec
- Application Security Process Spec
- Archiving Management Process Spec
- Asset Disposal Process Spec
- Asset Management Process Spec
- Audit Process Spec
- Background Checks Process Spec
- Backup Management Process Spec
- Business Continuity Management Process Spec
- Compliance Reporting Process Spec
- Consulting Process Spec
- Coordination and Segregation Process Spec
- Data Centre Management Process Spec
- Environments and Lifecycles Specs
- Hardening Process Spec
- Identity Management Process Spec
- Information Operations Process Spec
- Insurance Management Process Spec
- IT and Security Architecture Process Spec
- Knowledge Management Process Spec
- Malware Protection Process Spec
- Network Security Process Spec
- Patching Process Spec
- Penetration Test Process Spec
- Reputation Management Process Spec
- Risk and Maturity Assessment Process Spec
- Security Awareness Process Spec
- Security Incident Detection and Investigation Process Spec
- Security Incident Management Process Spec
- Security Procurement Process Spec
- Workload Schedule and Metrics and Reports Process Spec
Templates
- Agreement Template
- Audit Report Template
- Certification Report Template
- Incident Report Template
- Data Centre Maintenance Report Template
- Document Template
- Form Template
- Goal Assessment Report Template
- Information Security Portfolio Report
- Information Security Report Template.pptx
- Information Security Strategy Report Template
- ISMS Implementation Report Template
- Meeting Minutes Template
- Performance Report Template
- Policy Template
- Procedure Template
- Process Spec Template
- Risk and Information Security Meeting Minutes Template
- Service Hardening Procedure Template
- Strategy Report Template
- Third Party Hosting Agreement Template
O-ISM3 SECBOK is licensed for internal use or one client. If your company is planning to use O-ISM3 SECBOK for multiple clients, please contact for a consulting license.
Buy now your copy of O-ISM3 SECBOK and take your ISMS to new heights!
You will receive your copy of O-ISM3 SECBOK within 24h of purchase.
Please contact for questions, feedback or requests.